Crack Rdp Windows 2008 R2
- Posted in:
- 08/11/17
- 48
Grocotts Mail Friday, 10 October 2008. News. News in brief Cops swoop on drug dealers Grahamstown police confiscated R1 000 worth of crack cocaine and arrested. Photoimpression 4 Chip more. Enable Multiple User AccessConcurrent User Sessions For Remote Desktop on Windows 7. UpdateStar is compatible with Windows platforms. UpdateStar has been tested to meet all of the technical requirements to be compatible with Windows 10, 8. Windows 8. Despus de haber estado jugando con WhatsApp para encontrar una forma de saber si alguien haba ledo o no los mensajes, empezamos a jugar con los grupos. Removing vulnerable cipher on Windows 1. RDPIll share my answer from a Tech. TrustWaves vulnerability scanner fails a scan due to a Windows 10 machine running RDP Block cipher algorithms with block size of 64 bits like DES and 3DES. Net thread but first BLUF Serverfault conclusion Most likely you have some other difference in between the systems. Youre connecting between different OS versions, one system has FIPS enabled and the other does not, or you have different cipher restrictions in place under HKEYLOCALMACHINESYSTEMCurrent. Control. SetControlSecurity. ProvidersSCHANNELCiphers. I would certainly enable the SCHANNEL logging on the system that does work to determine which cipher is in use. Would love to hear back if you somehow got RDP to work with an alternate cipher. Copy of post We got it to workApparently 2. HKEYLOCALMACHINESYSTEMCurrent. Control. SetControlSecurity. ProvidersSCHANNELCiphersTriple DES 1. And the key on 2. HKEYLOCALMACHINESYSTEMCurrent. Control. SetControlSecurity. ProvidersSCHANNELCiphersTriple DES 1. I can confirm that use of Triple DES 1. DOES NOT disable 3. DES on the system. You can prove this to yourself with a protocol scanner like Nessus or by enabling SCHANNEL logging HKEYLOCALMACHINESYSTEMCurrent. How-to-deploy-a-terminal-server-running-Windows-Server-2008-R2-010.png' alt='Crack Rdp Windows 2008 R2' title='Crack Rdp Windows 2008 R2' />Control. SetControlSecurity. ProvidersSCHANNEL Event. Loggingdword 0. adaptateur USB to SATAIDE epson L110 series. Microsoft is announcing the availability of updates for supported editions of Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows RT. Windows 10 srmleri karlatrma tablosu. Windows 10 srmlerinin destekledii zellikleri renmek istiyorsanz bu yazy ve tabloyu referans. Oxid. it web site. Cain Abel v4. 9. 56 released Added Windows Vault Password Decoder. Crack Rdp Windows 2008 R2' title='Crack Rdp Windows 2008 R2' />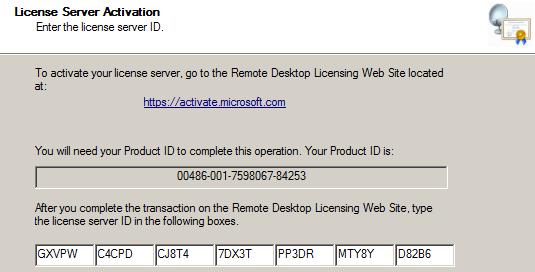 You will then have events in the SYSTEM log for example An SSL client handshake completed successfully. The negotiated cryptographic parameters are as follows. Protocol TLS 1. 0 Cipher. Suite 0x. 2f Exchange strength 1. For me the result is 0xa which Google reveals as TLSRSAWITH3. DESEDECBCSHA. When I use Triple DES 1. System event ID 3. RDP session is blocked. Per the article System cryptography Use FIPS compliant algorithms for encryption, hashing, and signing. Remote Desktop Services RDS. For encrypting Remote Desktop Services network communication, this policy setting supports only the Triple DES encryption algorithm. Crack Rdp Windows 2008 R2' title='Crack Rdp Windows 2008 R2' />Per the article System cryptography Use FIPS compliant algorithms for encryption, hashing, and signing security setting effects in Windows XP and in later versions of Windows. This setting also affects Terminal Services in Windows Server 2. Windows. The effect depends on whether TLS is being used for server authentication. If TLS is being used for server authentication, this setting causes only TLS 1. By default, if TLS is not being used, and this setting is not enabled on the client or on the server, the Remote Desktop Protocol RDP channel between the server and the client is encrypted by using the RC4 algorithm with a 1. After you enable this setting on a Windows Server 2. The RDP channel is encrypted by using the 3. DES algorithm in Cipher Block Chaining CBC mode with a 1. The SHA 1 algorithm is used to create message digests. Wwe 2005 Game Pc more. Clients must use the RDP 5. So both of these support the idea that RDP can only utilize 3. DES. However, this article suggests a larger range of ciphers is available FIPS 1. Validation. The set of cryptographic algorithms that a Remote Desktop Protocol RDP server will use is scoped to. CALGRSAKEYX RSA public key exchange algorithm. CALG3. DES Triple DES encryption algorithm. CALGAES1. 28 1. AES. Boss Me-50 Patch List. CALGAES2. AES. CALGSHA1 SHA hashing algorithm. CALGSHA2. 56 2. SHA hashing algorithm. CALGSHA3. 84 3. SHA hashing algorithm. CALGSHA5. 12 5. SHA hashing algorithm. Ultimately its not clear whether RDP can support non 3. DES protocols when FIPS mode is enabled but evidence would suggest it doesnt. I see no evidence that Server 2. R2 would function differently from Server 2. R2, however it does seem that Server 2. R2 was based around FIPS 1. Server 2. 01. 2 R2 follows FIPS 1. Server 2. 01. 2 R2 supports additional protocols. Youll note the additional protocols in the FIPS 1. Validation link. In conclusion I dont think Server 2. R2 can support RDP in FIPS mode with 3. DES disabled. My recommendation is to ascertain whether your system meets the conditions for a SWEET3. GB sent in a single session and whether disabling 3. DES is worth removing RDP capability. Other utilities exist to manage servers beyond RDP especially in a world where virtualization is highly commonplace.
You will then have events in the SYSTEM log for example An SSL client handshake completed successfully. The negotiated cryptographic parameters are as follows. Protocol TLS 1. 0 Cipher. Suite 0x. 2f Exchange strength 1. For me the result is 0xa which Google reveals as TLSRSAWITH3. DESEDECBCSHA. When I use Triple DES 1. System event ID 3. RDP session is blocked. Per the article System cryptography Use FIPS compliant algorithms for encryption, hashing, and signing. Remote Desktop Services RDS. For encrypting Remote Desktop Services network communication, this policy setting supports only the Triple DES encryption algorithm. Crack Rdp Windows 2008 R2' title='Crack Rdp Windows 2008 R2' />Per the article System cryptography Use FIPS compliant algorithms for encryption, hashing, and signing security setting effects in Windows XP and in later versions of Windows. This setting also affects Terminal Services in Windows Server 2. Windows. The effect depends on whether TLS is being used for server authentication. If TLS is being used for server authentication, this setting causes only TLS 1. By default, if TLS is not being used, and this setting is not enabled on the client or on the server, the Remote Desktop Protocol RDP channel between the server and the client is encrypted by using the RC4 algorithm with a 1. After you enable this setting on a Windows Server 2. The RDP channel is encrypted by using the 3. DES algorithm in Cipher Block Chaining CBC mode with a 1. The SHA 1 algorithm is used to create message digests. Wwe 2005 Game Pc more. Clients must use the RDP 5. So both of these support the idea that RDP can only utilize 3. DES. However, this article suggests a larger range of ciphers is available FIPS 1. Validation. The set of cryptographic algorithms that a Remote Desktop Protocol RDP server will use is scoped to. CALGRSAKEYX RSA public key exchange algorithm. CALG3. DES Triple DES encryption algorithm. CALGAES1. 28 1. AES. Boss Me-50 Patch List. CALGAES2. AES. CALGSHA1 SHA hashing algorithm. CALGSHA2. 56 2. SHA hashing algorithm. CALGSHA3. 84 3. SHA hashing algorithm. CALGSHA5. 12 5. SHA hashing algorithm. Ultimately its not clear whether RDP can support non 3. DES protocols when FIPS mode is enabled but evidence would suggest it doesnt. I see no evidence that Server 2. R2 would function differently from Server 2. R2, however it does seem that Server 2. R2 was based around FIPS 1. Server 2. 01. 2 R2 follows FIPS 1. Server 2. 01. 2 R2 supports additional protocols. Youll note the additional protocols in the FIPS 1. Validation link. In conclusion I dont think Server 2. R2 can support RDP in FIPS mode with 3. DES disabled. My recommendation is to ascertain whether your system meets the conditions for a SWEET3. GB sent in a single session and whether disabling 3. DES is worth removing RDP capability. Other utilities exist to manage servers beyond RDP especially in a world where virtualization is highly commonplace.